Meet federal, state, and industry
information security regulations instantly
Since security breaches can cause serious damage, the relationship between information security and the economic growth of businesses has been subject of many research studies. [1] [2] 3 [4]
The corresponding economic model, proposed by Lawrence A. Gordon and Martin P. Loeb in 2002, implies that:
- If data were perfectly invulnerable, then no investment in information security would be made,
- At some sufficiently larger level of vulnerability, it would be optimal to make a positive investment in information security measures in order to reduce the probability of data loss, and therefore the expected monetary loss.
Optimal information security policy should incorporate both possible approaches:
- A reactive one — having a well-defined vulnerability assessment strategy,
- And a proactive one — application of currently available computer protection mechanisms, or countermeasures, in order to prevent, eliminate, or minimize the impact of security flaws.
Though security vulnerabilities are difficult or even impossible to predict, many of them require multiple conditions to be met at once in order to be successfully exploited:
- For example, attackers tend to mask their presence on the target system while exploiting a security flaw. For this reason, they often target rarely used user accounts to perform — or attempt to perform — the attack under,
- Brute-force password guessing attacks have higher probability of success when shorter and dictionary-based passwords are used to secure some of the user accounts on the particular system,
- Some protocols, though reliable, have been designed to operate with information in plaintext (unencrypted) form. These typically provided sufficient security at the time they have been implemented, but are not sufficient any more.
All three of the provided conditions can be avoided using the same strategy — through application and enforcement of a security policy which fulfills the following criteria:
- Prevent retired user accounts from being reused,
- Define and enforce strong passwords based on multiple criteria such as length and character variety, insert a delay between unsuccessful login attempts, and track these attempts,
- And finally, forbid the use of protocols which are no longer considered secure.
In order to minimize the threat of an attack on computer infrastructure, or even completely prevent it, many institutions in both the private and public sectors have adopted the concept of enforcing a security policy or a security benchmark. These policies define security requirements which all systems used by the institution must meet. It applies not only to systems physically located within the organizations, but often to any third party environments have access to the organizations’ computer infrastructures. In some cases, these policies are defined by government regulations, but many businesses adopt their own security policies even if they are not specifically required to do so by law.
The specific requirements for security policy differ depending on the area of activity of a particular organization. For example, a solely private sector based cloud solutions provider will have different security norms, and will be required to fulfill different information security requirements by law, than a United States federal agency.
Despite the variety of the possible requirements, there are many common steps and procedures that any institution or business wishing to protect itself should perform. These include, but are not limited to:
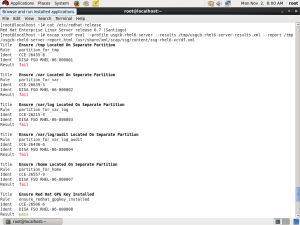
Determine the specific security baseline which the underlying computer infrastructure must comply with
Obtain a security checklist for the requirement(s) in a format suitable for machine processing
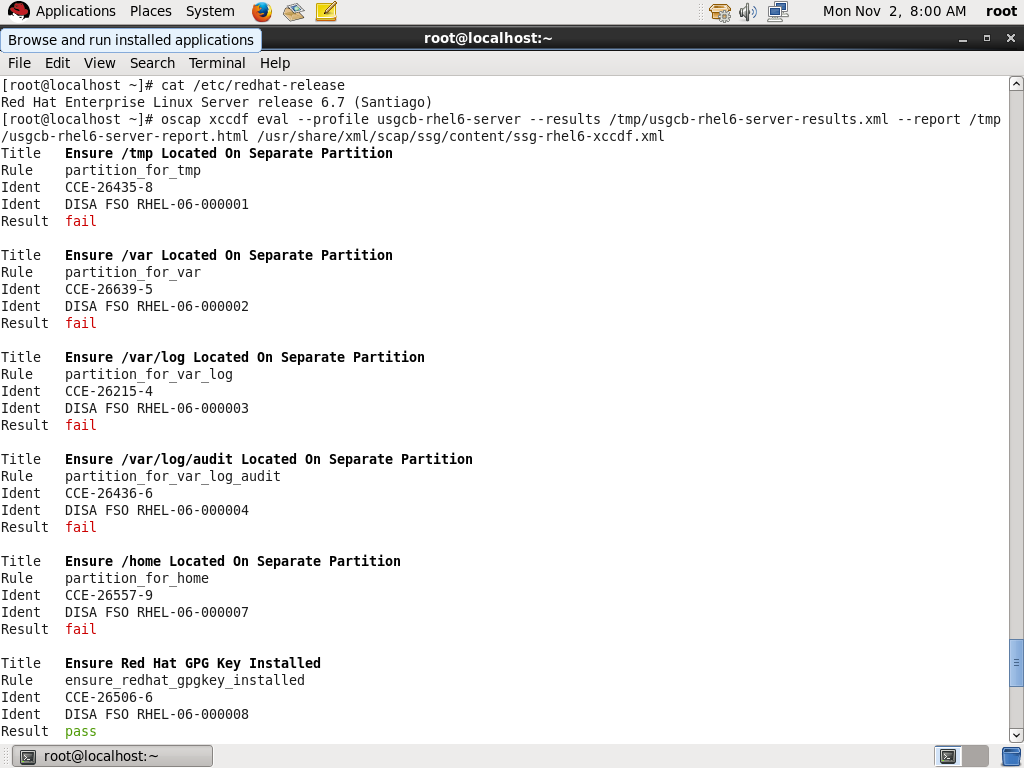
Quickly identify the current state of the computer infrastructure against the requirement(s)
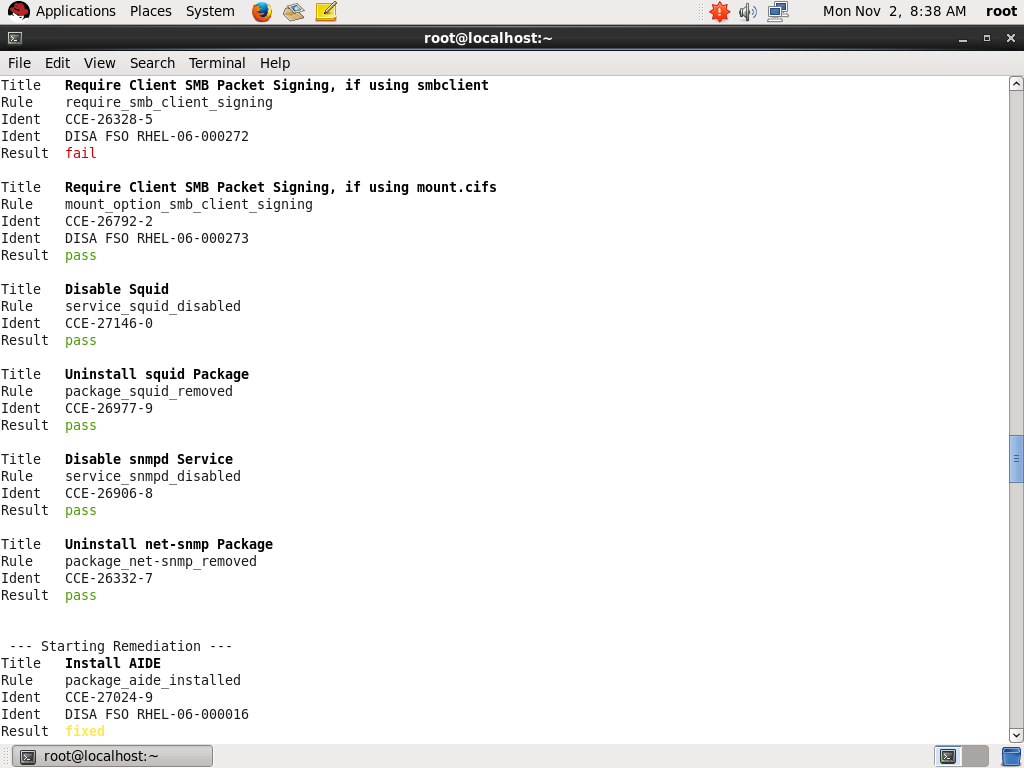
React promptly — perform corrective operations for requirements the system did not meet at a specific point in time
Prefer an automated approach — perform compliance analysis and corrective operations (remedial actions) in a machine-controlled, unattended way on a regular basis, regardless of the infrastructure’s complexity
Utilize proper software tools to carry out these tasks with minimal effort, and at the same time, attempt to reduce any required outage periods related to these tasks to a minimum.